Update 10/23/13: Read part three of my blog about 2013 Norton Report- Cybercrime: Insights from an HR Strategist
Update 10/18/13: Read part two of my blog about 2013 Norton Report- Mobile Cybercrime
Yours truly was asked to give a talk at Symantecs’ press event w/ online safety guru Philip Routley, for the 2013 Norton Cybercrime Report. There’s so much on the material, so I decided to make three blog posts out of their cyber crime report.
Sonnie Santos, gives a talk on PH cyber culture and online behavior
at Norton’s 2013 Report Press Briefing
This article will focus on the highlights and figures, the 2nd article will be about mobile cybercrime (either I update my mobile safety article or create a new one). And the third article will be about the growing need for companies to define and/or strictly enforce use of company issued device.

Belinda Lim, Symantec Group Manager for Asia South and Korea
So let’s get started with the key findings, as follows:
And those affected by cyber crime are
- Mobile device owners- 63%
- Social network users- 63%
- Those who use public hotspots- 68%
- Parents of kids aged 8-17 – 68%
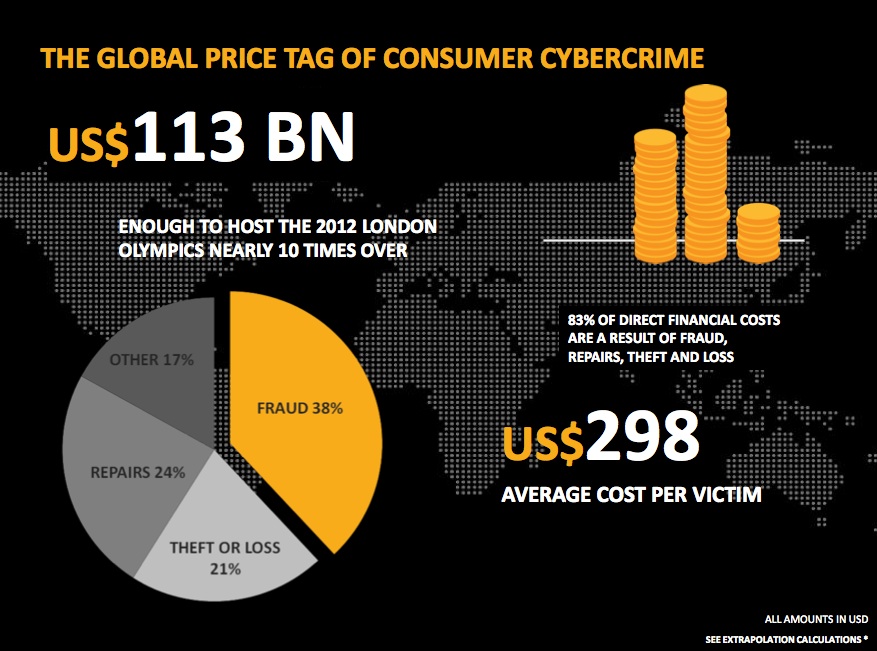
About 12 people are affected by cyber crime worldwide per second; 1 million per day and 378 million per year. The average cost of cyber crime per person is roughly P 12, 824.43 and annual cost of P 4.86T due to fraud, theft, loss and repairs.
About 50% of online adults were exposed to negative situation which include harassment and bullying, while 51% were victims of social engineering resulting to malware/virus infection, scams, hacking, fraud and theft.
The report showed that the main reason why the victims fell to cybercrime is because of their online behavior, partly an HR issue. These behaviors include:
- Preference of convenience over security
- Do not put password on their mobile device
- Do not log-out after accessing social networking accounts
- Use of company issued device for work and play *an HR issue
- Kids using parents’ work device (at times, company issued) for fun and play
- They connect w/ strangers on their social networking accounts
- They share their password w/ others
- They use the same cloud storage for both work/office and personal files

Philip Routley, Symantec’s Product Marketing Manager
My two scents
We believed that the best and 1st line of defense against cybercrime is education. Teaching internet users of the different risks and how they can protect themselves from cyber criminals. A change mindset will trigger a changed behavior. This will also result to intelligent choice to use online tools as 2nd and 3rd line of defenses.
As side note, this is the reason why since 2010, we are going to different academic institutions and various organizations to do exactly that- educate them of online risks and surf safe practices.
Discover more from ASKSonnie.INFO
Subscribe to get the latest posts sent to your email.